
By Graham Stroud and John Comben
Introduction
Cyber risk should be at or near the top of the pile when it comes to business and indeed personal risks.
We have recently seen in the news the crippling effect a cyber-attack had on a major foreign exchange company. In this case a criminal gang implanted ‘ransom ware’ resulting in much of the company’s services being taken down, with the gang demanding a ransom payment to enable restore.
Cyber risk is the likelihood of a cyber-attack on a company’s systems which could result in financial loss, reputational damage, and or regulatory sanction. There have been many examples in the recent news of attacks on company’s resulting in their systems being crippled, forcing services to be taken down or sensitive data being stolen. The risk of financial loss does not just impact company’s but also private individuals where information may be stored insecurely on a home PC.
Cyber-attacks can take many different forms, which include (but are not limited to):
- Ransomware – where a criminal finds a weakness in an organisation’s cyber security and is able to implant malevolent software which encrypts system data until a ransom is paid (often demanded as a crypto currency).
- Phishing – email is used to deceive the recipient into disclosing information or opening a hyperlink that takes the victim to a fake website where they may reveal confidential information (such as credit card details, pin numbers, passwords etc). Or it could download malware as a means to gain access to the victim’s company or personal system.
- Data breaches – where data is stolen for criminal purposes
- Malware – software loaded to a target organisation’s system which may corrupt data or take over a system (such as a website).
The list is long, and the risks must be treated seriously by companies. For the purposes of this article, the focus is on phishing and follows the lifecycle of an email, or more specifically, a suspicious email.
Identifying and investigating suspicious emails
The first question to address is how to identify a phishing email. These usually purport to be from a legitimate organisation and the perpetrators will make the email look genuine, they often copy their logo, colour scheme etc in an effort to fool the recipient.
There can be clues to look out for indicating an email may not be genuine:
- Is the message addressed personally, or is it generic e.g. ‘Dear Customer’ – remember banks and other legitimate companies would not contact a customer asking for sensitive information via email or cold call!
- Phishing emails can be poorly worded – often the grammar and spelling are poor.
- The email address of the sender is likely to be similar to the legitimate company but not the same – take care to check this carefully.
- The web address of the sender or any link will be similar to but not the same as the legitimate company – take care to verify this.
- The message will often be written in a way to scare you – something ‘bad’ has happened and the recipient is made to feel pressured into providing this or that information or click on the embedded link in order to resolve.
A simple rule of thumb – if in doubt, report the email as suspicious!
To help protect an organisation from the risk of phishing, a ‘Plug In’ is available from third party providers enabling a company to simplify the process the recipient of a suspicious email has follow in order to validate or delete it.
All too often, the alternative relies on a manual process whereby the recipient sends a suspicious email to an internal security email address for review. This is not ideal – people can forget the security email address, or fail to delete the suspicious email, leaving it in their email system waiting for them to action it by mistake.
An automated approach for managing and investigating suspicious emails
The following tables outline steps that are followed when using an email plug in, based on the recent delivery of such by MHC to a major banking client.
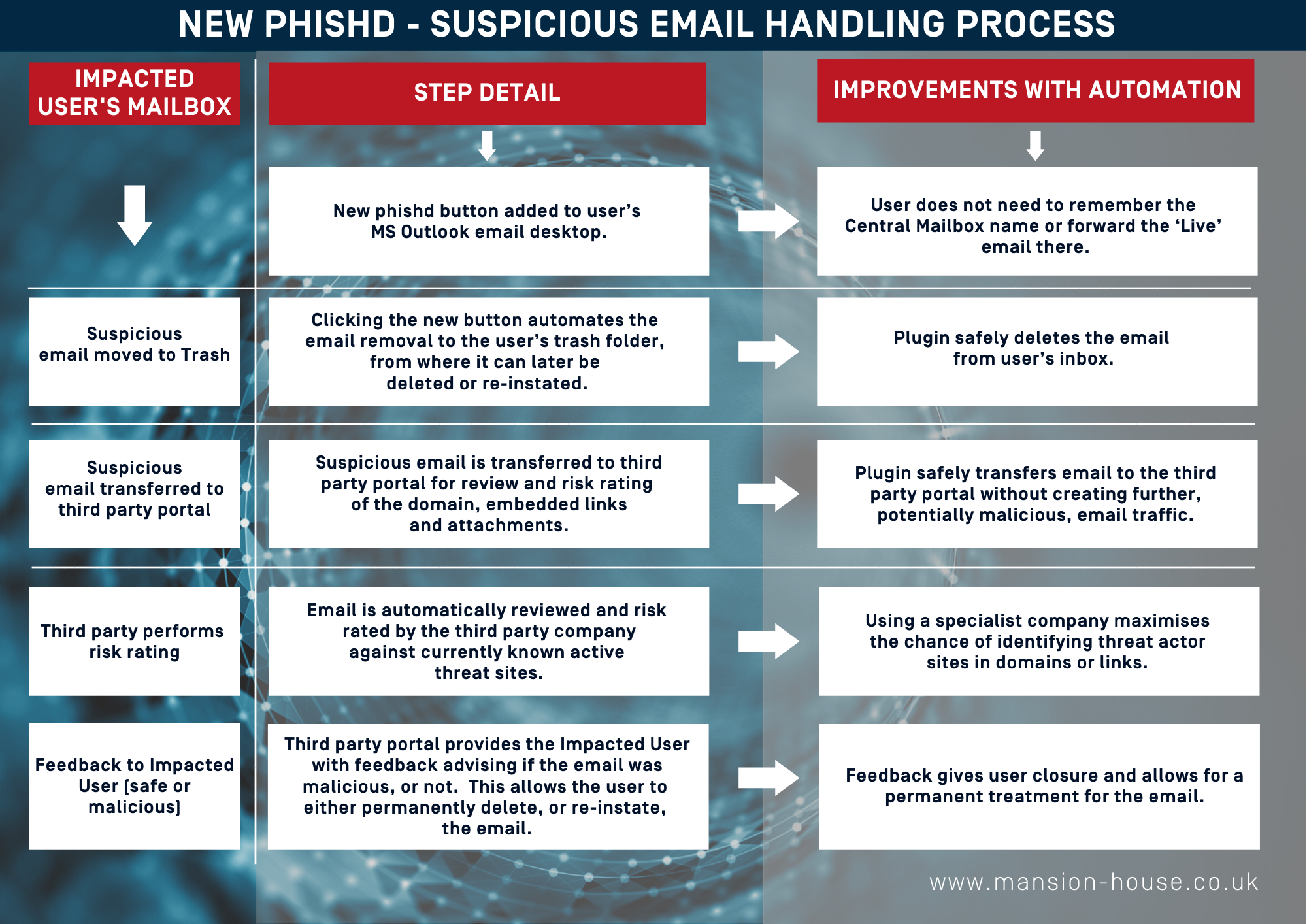
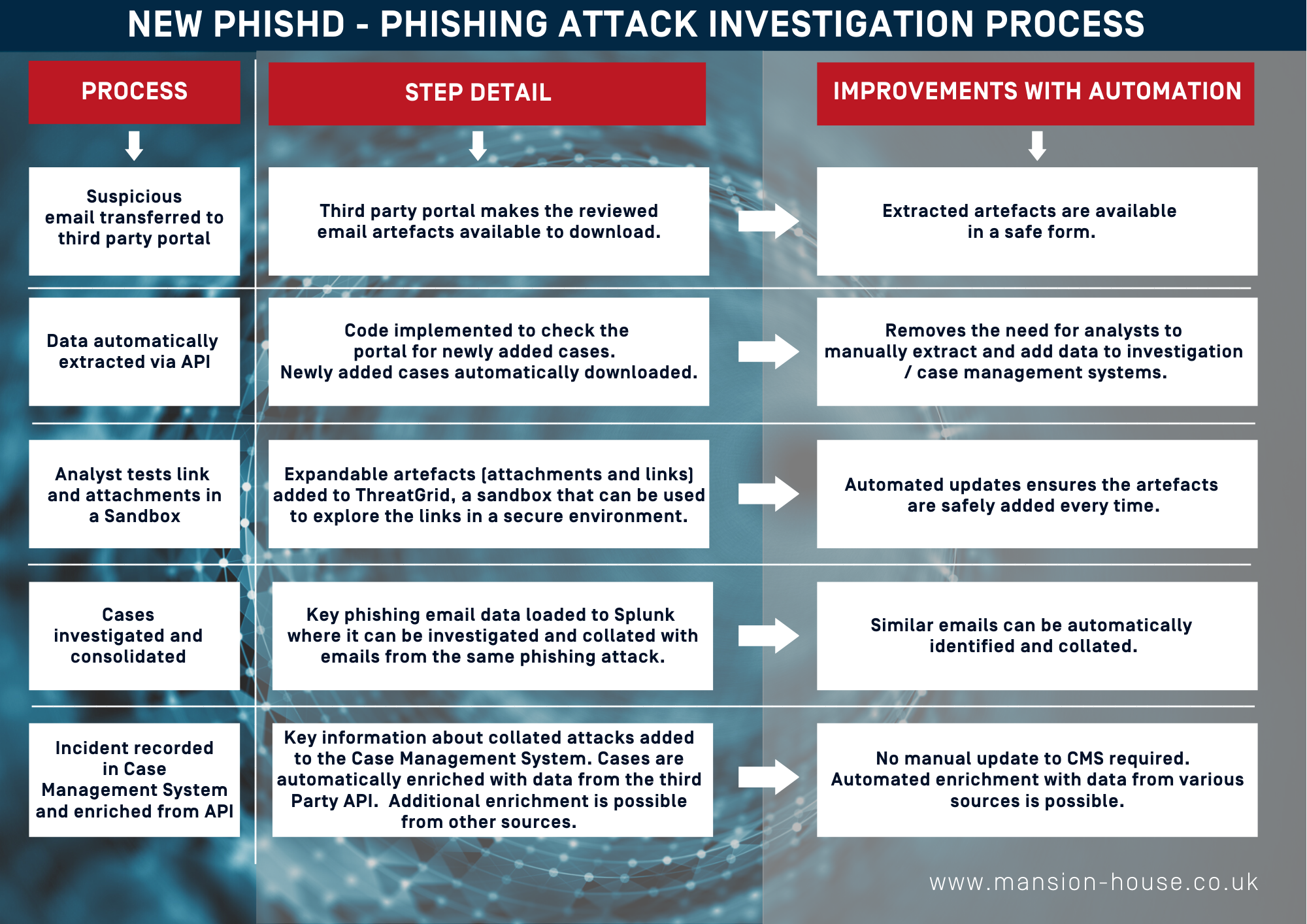
Summary
Phishing is a real and present danger to organisations and individuals. Organisations can take steps to better protect their business by using tools to automate the checking of suspicious email.
MHC has strong experience in deploying such solutions and are ready to discuss client needs and work with them to identify and deploy the right solution.



